Integrating AbuseIPDB with Polarity Community Edition - Instant AbuseIPDB


Integrating AbuseIPDB with Polarity Community Edition - Instant AbuseIPDB
AbuseIPDB + Polarity Community Edition Integration Tutorial
1.) Pre-Requisites:
- An AbuseIPDB API account
- Polarity Community Edition 7.4.0 or newer NOTE: At the time of writing, the latest Polarity Community Edition release is 7.4.0
2.) Introduction:
If you are familiar with AbuseIPDB and Polarity Community Edition, you can skip this section and go to the next section.
AbuseIPDB provides a free API for reporting and checking IP addresses. Every day webmasters, system administrators, and other IT professionals use our API to report thousands of IP addresses engaging in spamming, hacking, vulnerability scanning, and other malicious activities in real time.
Polarity, either Community or Enterprise editions, is an overlay, or widget, that has access to and and aids with your existing workflow. Polarity comes with over 100 integrations to extend the power of the platform. This section will guide you through the initial steps of activating and using the AbuseIPDB integration for the Polarity Community Edition. For more info on what the Polarity is, see Polarity Platform Documentation. If you are unfamiliar with Polarity and don't have time to read the full documentation, the key takeaway of Polarity is:
- Increased Productivity
- Search once and know everything your enterprise knows about a piece of data, both internally and externally, with Polarity client.
- What used to take 50 tabs, now takes just 1 tab and 2 seconds, the copy function, so you can focus on getting the job done, not searching for context.
About Polarity Community Edition:
3.) Install the Polarity Client
This guide assumes you have some version of the Polarity client setup. Polarity supports Windows, macOS, and Linux. Community Edition is free to use and is available for download from the Polarity website. The most recent release version at the time of writing is Polarity Community Edition 7.4.0, so guide should be compatible with Polarity Community Edition version 7.4.0 and later.
If you do not have the Polarity client installed, you can download it from the
Polarity Community Edition website.
NOTE: While this guide is not designed to work with Polarity Enterprise Edition, it should also
work with Polarity Enterprise Edition. However, this guide does not cover the expanded features of the
Enterprise Edition. For a guide on Polarity Enterprise Edition,
visit the Polarity Enterprise Edition website.
4.) Steps for Configuring and connecting Polarity to AbuseIPDB Integration through the client
After installation, launch the client. If this is your first time launching the Polarity Desktop Client. NOTE: your login credentials are provided in your welcome email from Polarity.
For the code to the Polarity Community Edition integration with AbuseIPDB, visit GitHub.
Integrating AbuseIPDB with your Polarity setup enriches your overlay with detailed IP reputation insights, making it a powerful tool for real-time threat intelligence and analysis.
-
Create an API key in your AbuseIPDB account.
NOTE: Ensure your API usage complies with AbuseIPDB's guidelines to maintain access and prevent service disruptions. - The AbuseIPDB integration comes standard with Polarity Community Edition. To configure the integration:
- Open the Polarity client
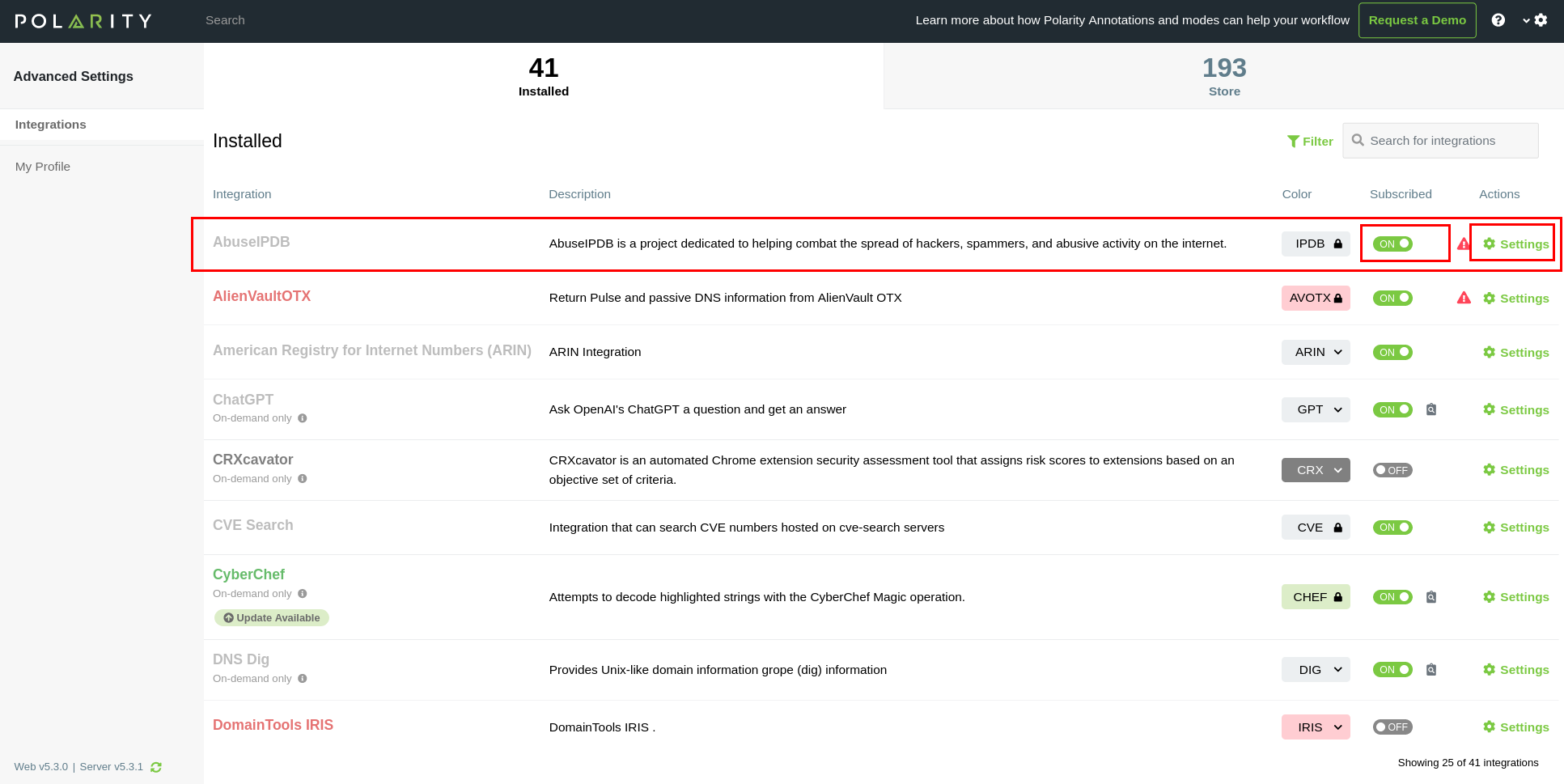
- Navigate to the settings page by clicking the gear icon in the top right corner of the client, opening the dropdown, and selecting the Advanced settings option. See figure 1.
- Make sure the switch is flipped to the on position, this enables the AbuseIPDB integration. See figures 2 and 3.
- Select settings, so you can see the AbuseIPDB specific settings:
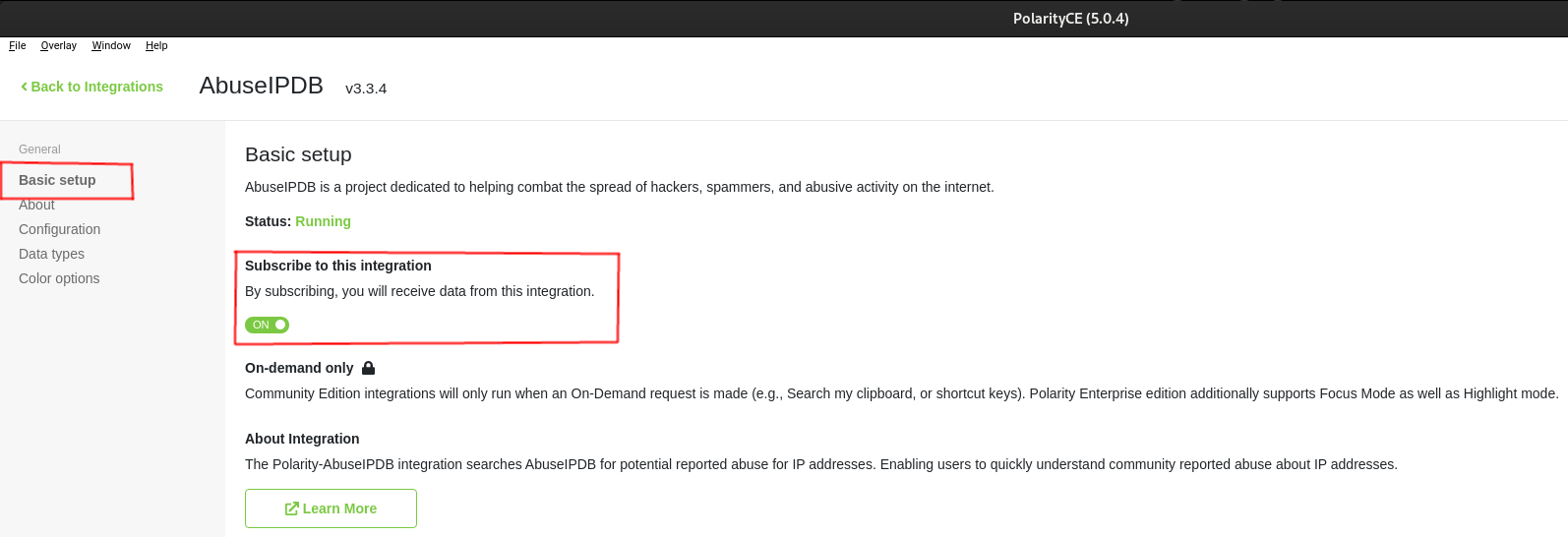
- Basic Setup: This is where you can enter your API key and configure the overlay. From here, you can enter your AbuseIPDB API key and configure the overlay from here
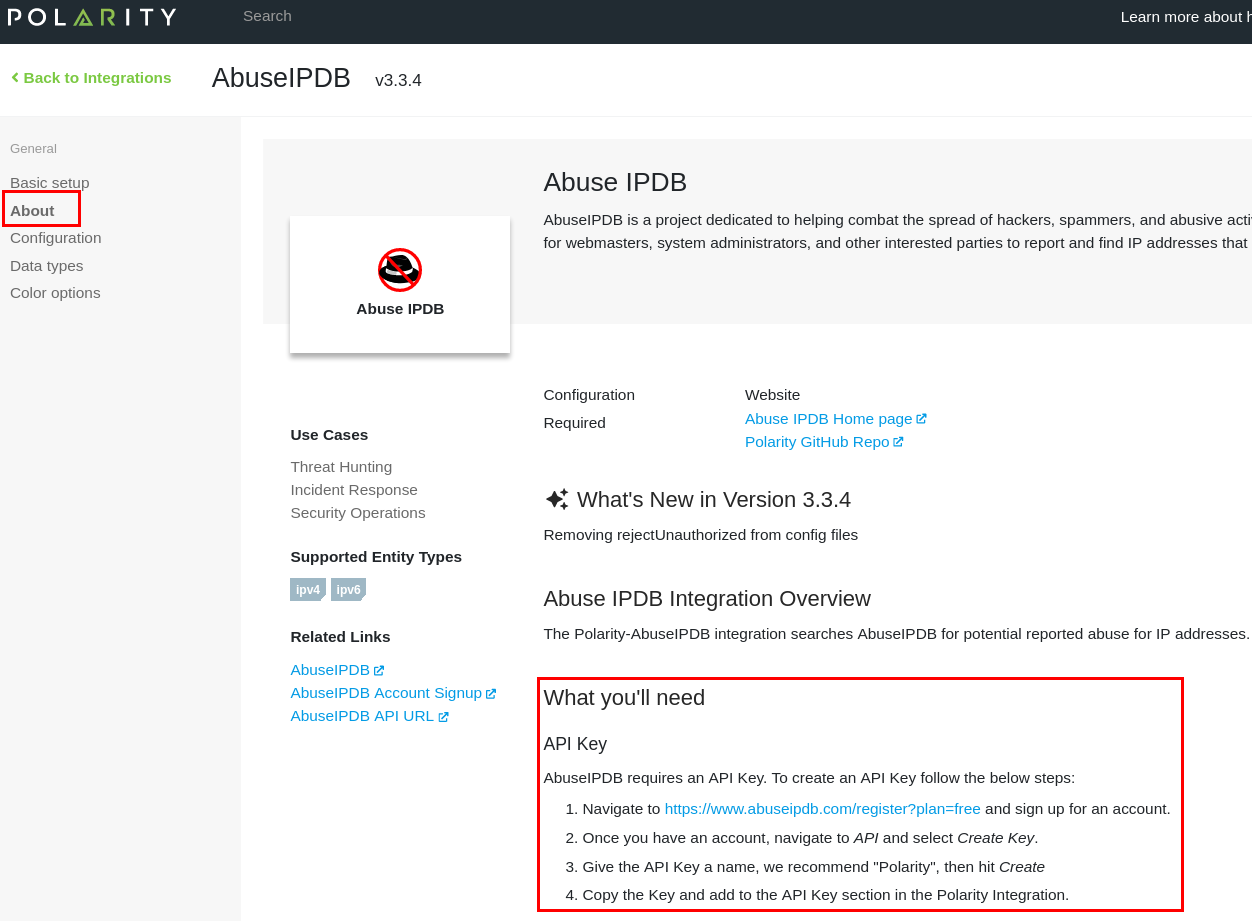
- About: Here you find the official instructions for configuring the AbuseIPDB integration. Also, examples and key details are provided. You can explore the other options in the settings menu as well. However usage is limited with the community version.
- Restrictions: Because of differences between the Community Edition and the Enterprise Edition of Polarity, It is important to note that the AbuseIPDB integration is only available in On-Demand resource mode in the Community Edition. You must have Polarity Enterprise Edition to use the other recognition modes.
Now that you have completed the tutorial, you can use your Polarity client to search for IP addresses and gain insights from AbuseIPDB's check endpoint and massive database. Data like reputation data, confidence scores, and detailed attack reports, are now available instantly, from any part of your workflow. Polarity now gives you instant AbuseIPDB massive dataset, simply use the copy function, on any IP address and Polarity will automatically search, find, and return all available data from ABuseIPDB. In Polarity, the paste function is not even needed, search is automatically triggered on the copy function.
5.) Practical Examples:
Maximizing Threat Response Time with AbuseIPDB and Polarity Community Edition
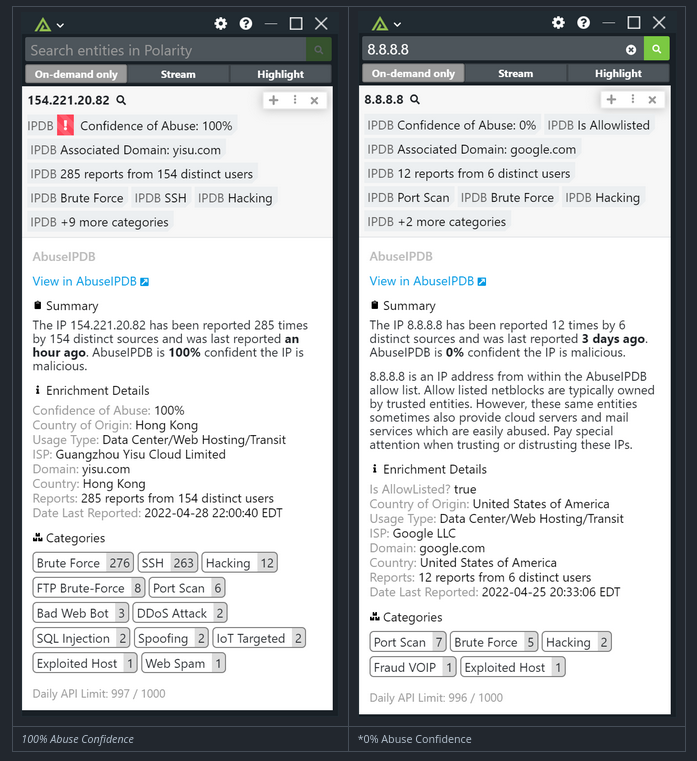
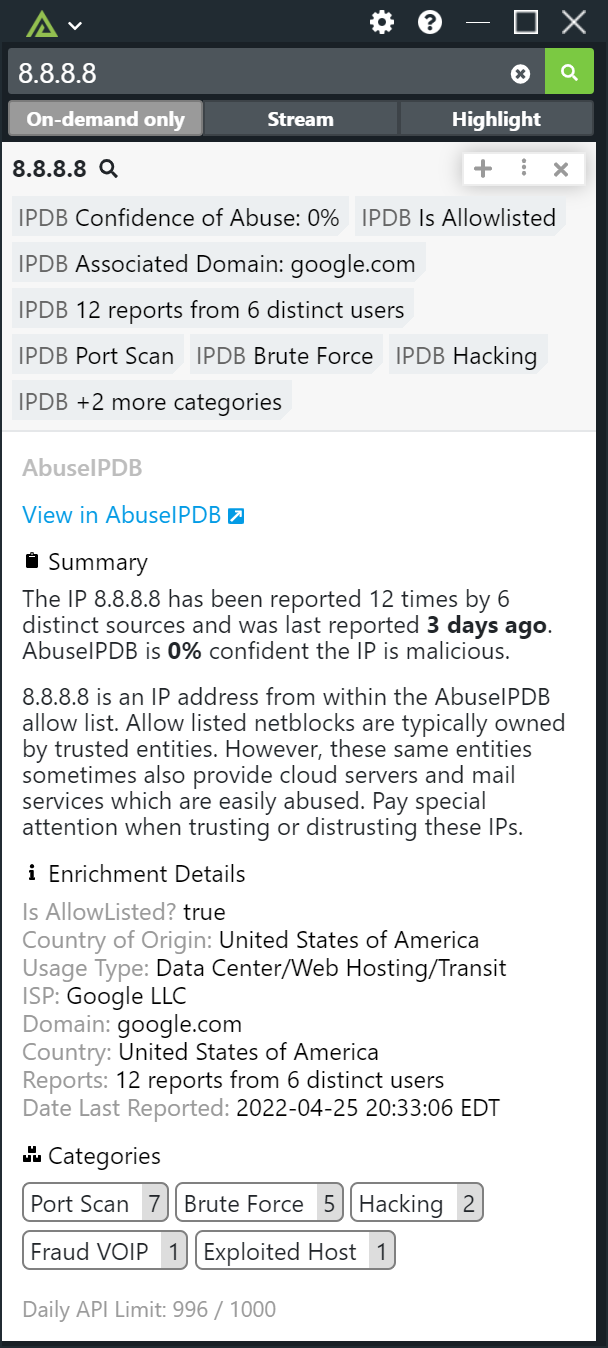
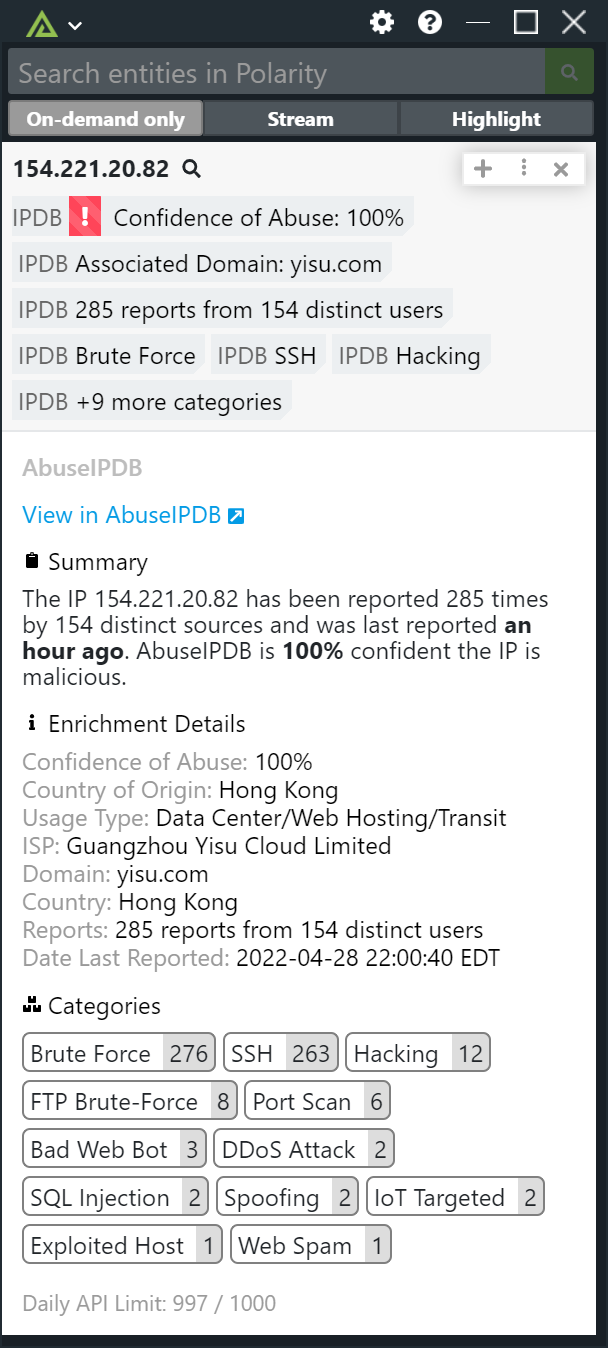
By leveraging AbuseIPDB's API, Polarity Community Edition users can instantly access detailed IP reputation data, including confidence scores, reports and more. The integration of AbuseIPDB with Polarity Community Edition allows security teams to access critical IP reputation data seamlessly within their existing workflows, enhancing decision-making and response times.
In figure 9, we see an image of a Polarity's overlay, with AbuseIPDB's reputation data, being used side by side with Wireshark, Etherape, and ss to check network traffic.
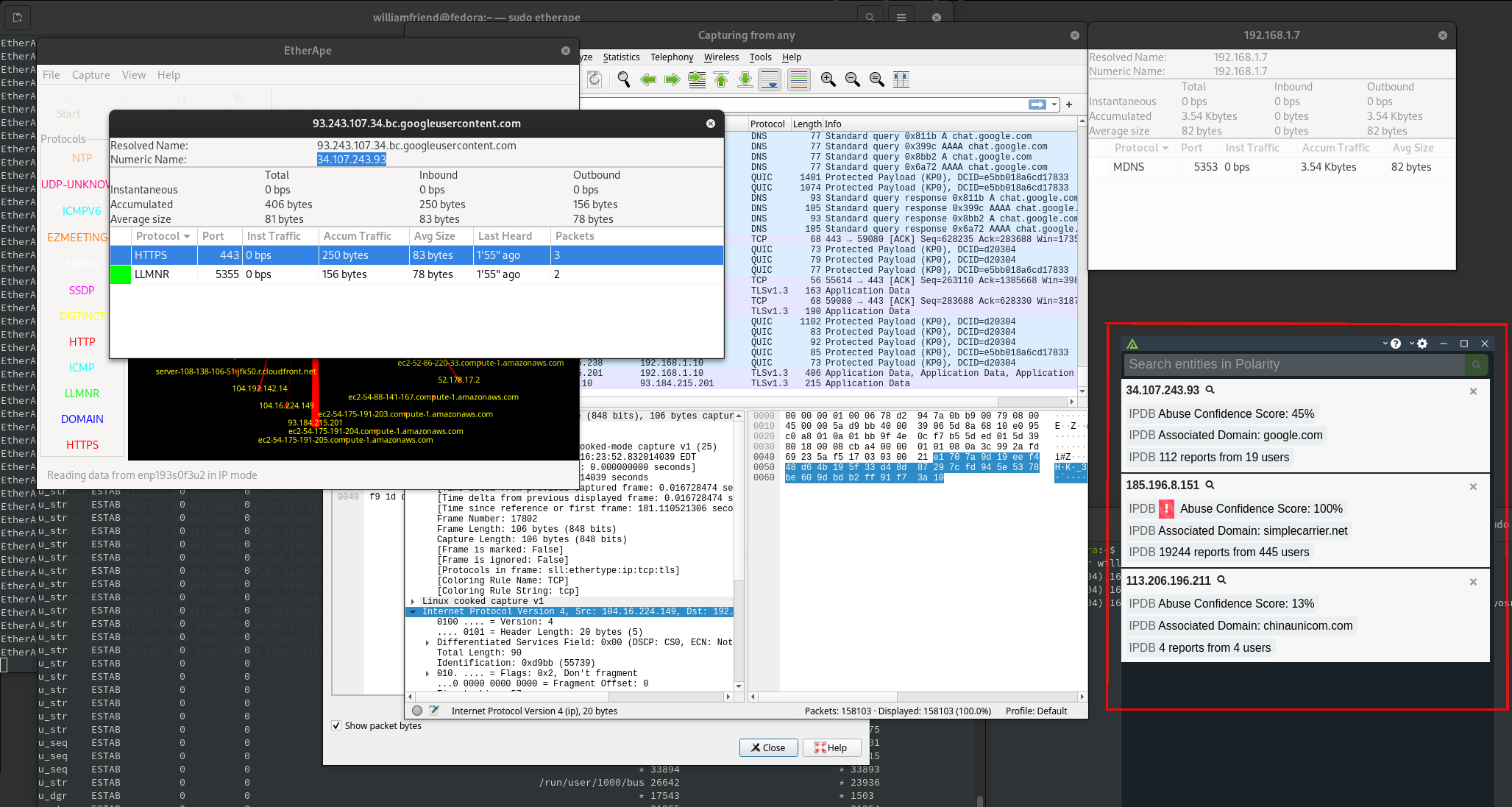
The concept in figure 9, can be applied to any part of your workflow that you use to monitor ip addresses in your network. When you click on any of the 3 cards from figure 9, you get an expanded view of the data, like in figure 10:
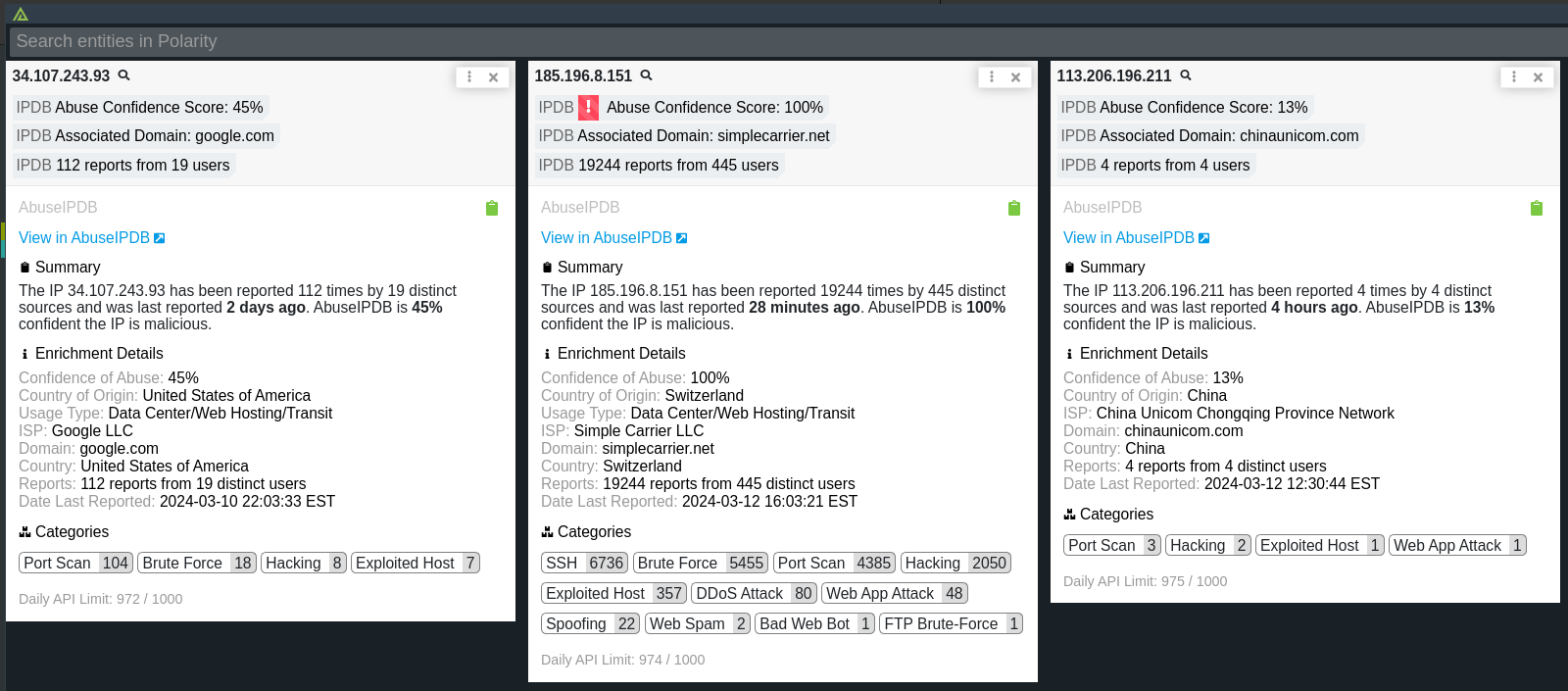
6.) Other Resources:
The source code repository for the Polarity Community Edition and AbuseIPDB integration is available on Github.
For more on Polarity integrations, visit the Polarity Github page.
Polarity has recognition modes, however the AbuseIPDB integration is only available in On-Demand resource mode in Polarity Community Edition. You need Polarity Enterprise Edition to use the other recognition modes. For more on On-Demand resource mode, in the Polarity Community Edition, visit the Polarity Community Edition Guide. For more on the recognition modes in the Polarity Enterprise Edition, visit the Polarity Enterprise Edition Guide.
For specific information on the AbuseIPDb check endpoint, that the Polarity Community Edition uses to query the AbuseIPDB API, visit the AbuseIPDB API documentation.
For more on the AbuseIPDB API, visit the AbuseIPDB API documentation.
7.) Page Feedback
If you have any feedback or questions about this page, please contact us, and let us know. We are always looking to improve the content and resources we provide to our users.